With financial and health records having gone almost entirely digital, it’s easy to see why the field of cybersecurity has emerged as one of the most in-demand tech professions. Cybersecurity professionals protect consumers’ personal information, safeguard against cyberattacks, and promote safer web browsing habits so organizations and private citizens can protect themselves from identity theft and other attacks.
Most people understand that cybersecurity professionals protect our information from hackers. But how they actually do that is less widely understood.
That’s why we’ve created this guide. Below, we’ll detail everything you need to know about cybersecurity so that you can better understand how this industry is shaping tomorrow’s world.
What Is Cybersecurity?
Cybersecurity is the practice of protecting systems, networks, and programs from cyberattacks and unauthorized access. Cyberattackers aim to destroy, alter, or access sensitive information for financial gain or to disrupt regular business operations. A cybersecurity strategy uses people, processes, and technology to safeguard an organization’s intellectual property and other important digital assets.
Why Does Cybersecurity Matter?
Cyberattacks cost organizations millions of dollars each year and lead to reputational damage. Organizations experience an average of 130 cyberattacks each year. In 2021, the global cost of cybercrime exceeded $6 trillion, and the problem is getting worse. According to Accenture, the average annual number of security breaches grew by 27.4% in 2020.
Data breaches also pose grave consequences for the average person. Cybercriminals use stolen personal information, such as a social security number, to impersonate someone, usually with the end goal of seizing their financial assets. Attackers also mount phishing attacks on personal computers and mobile devices to infect the device with malware—software designed to disrupt, damage, or gain unauthorized access to a system.
Companies need cybersecurity professionals for several reasons. These professionals play critical roles in protecting sensitive information, defending against cyber threats, and maintaining the security and integrity of computer systems and networks.
Their jobs include:
- Protecting sensitive information
- Defending against cyber threats
- Maintaining the security of critical infrastructure
- Ensuring business continuity
- Enhancing network security
- Collaborating with security analysts
- Adhering to regulatory compliance
- Addressing insider threats
- Evaluating and implementing cybersecurity solutions
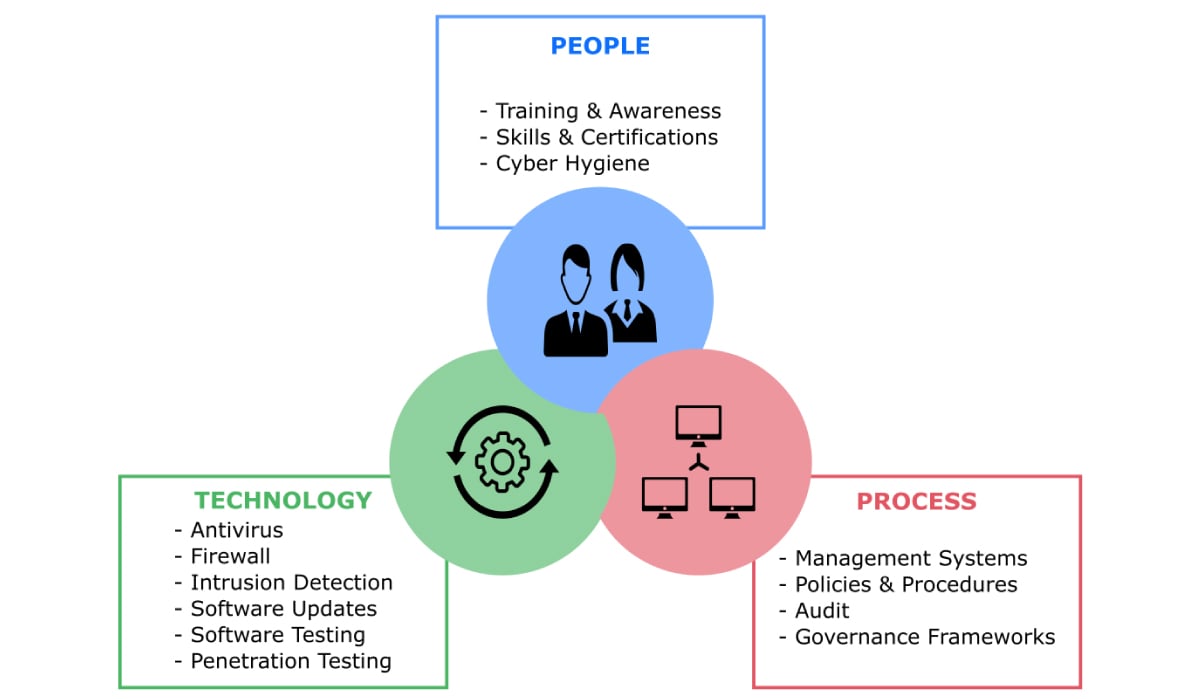
Three Pillars of Cybersecurity: The Foundation of Effective Cybersecurity
Source: GitHub
Cybersecurity is a framework that requires the marshaling of resources in a coordinated manner. Let’s break down what that looks like:
- People: Organizations hire trained cybersecurity professionals to design and implement cybersecurity frameworks. They must also train their employees to recognize phishing scams and social engineering. People are almost always the weakest link in an organization’s cyber resiliency.
- Processes: Processes and policies provide the frameworks for cybersecurity governance. These processes range from preventative strategies to avoid cyberattacks to real-time interventions in the event of cybercrime to identify and eliminate an intruder.
- Technology: Technology refers to the IT infrastructure (hardware and software) organizations use to achieve cybersecurity. Examples include antivirus software and defensive AI that scans computer networks for anomalous behaviors and learns from prior cyberattacks. Cloud encryption technology secures data stored in the cloud by turning the information into unreadable code before it is stored.
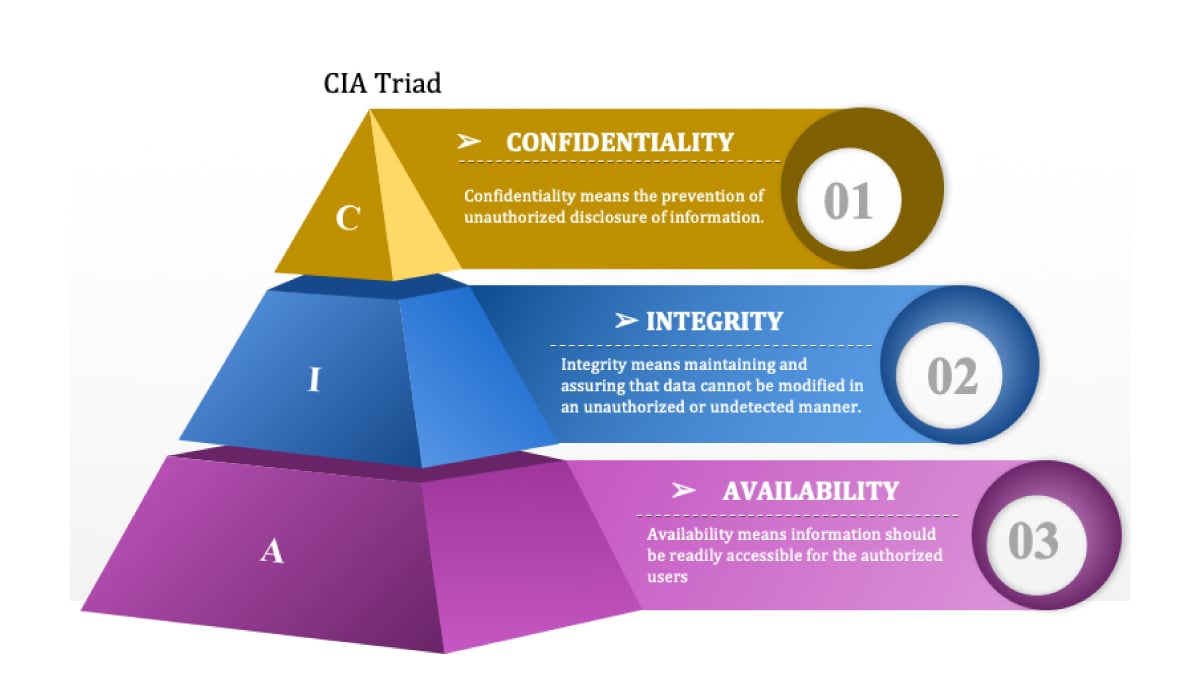
CIA Triad: The Three Primary Objectives of Cybersecurity
Source: Facebook
The CIA triad is a common model that explains the main objectives of any cybersecurity framework. This model helps security teams ensure all bases are covered using security best practices.
- Confidentiality: Organizations must protect proprietary information and their consumer’s personal data. Access must be restricted to authorized users, and robust authentication protocols and user permission controls are needed to keep intruders out. For example, employees in unrelated departments should not have access to certain data because it could be liable to exploitation.
- Integrity: Data must be accurate, trustworthy, and free from tampering. Data integrity can be maintained with access control and encryption. In some cases, data may be protected physically from outside sources that might corrupt it (particularly for businesses that use on-premise servers rather than cloud storage).
- Availability: Ensuring systems, applications, and networks are functioning normally and haven’t been shut down by attackers. Data should be available to authorized users whenever they require it.
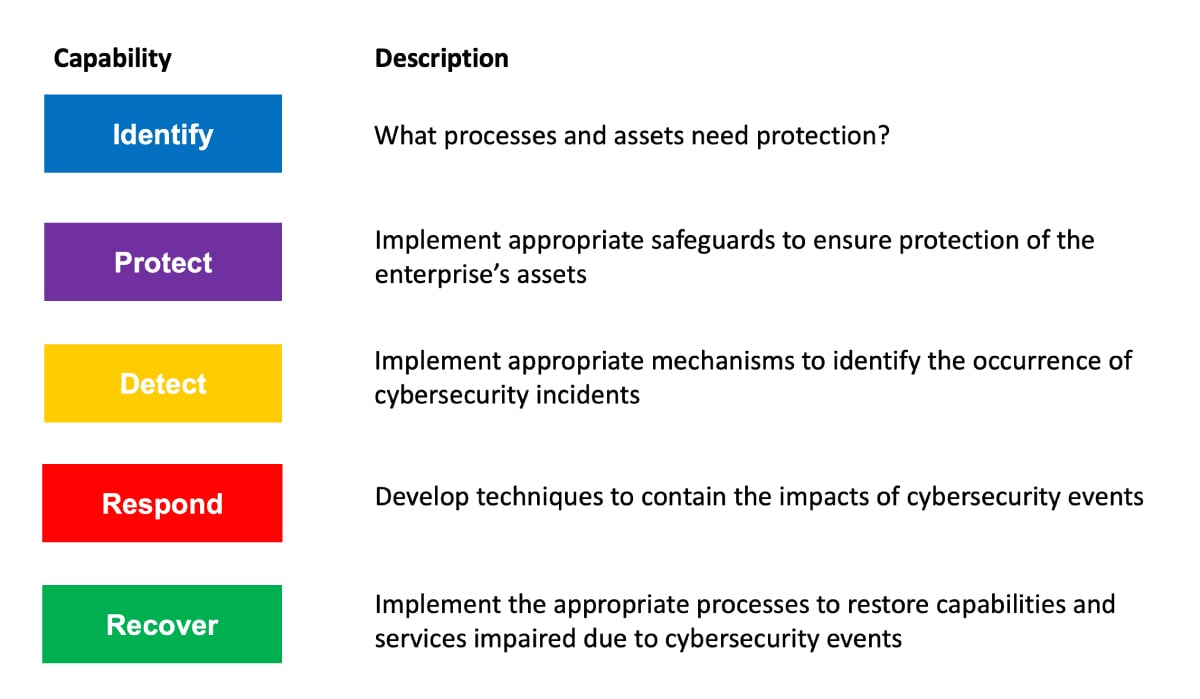
The Cybersecurity Process (NIST Cybersecurity Framework)
Source: Balbix
The NIST framework consists of standards, guidelines, and best practices to mitigate cybersecurity risk. The framework comes from the National Institute of Standards and Technology, a government agency formed by the U.S. Department of Commerce that develops cybersecurity standards for businesses, federal agencies, and the broader public. Here’s what that looks like in practice:
- Identify: Determine the nature of the threat and identify the assets that need protection.
- Protect: Implement appropriate security controls to protect the compromised asset and restore system function.
- Detect: Determine the nature and impact of the threat. Implement continuous monitoring capabilities to track security events and see if protective measures are working.
- Respond: Develop techniques to oust the intruder and limit the impact of the threat (threat containment).
- Recover: This is the process of restoring any systems and services that were impaired during the attack and implementing improvements based on lessons learned.
Cybersecurity Types
Source: Public Health Notes
Cybersecurity can be categorized into five distinct strategies. Organizations often need a combination of approaches to secure themselves.
- Network Security: Network security is about protecting an organization’s computer networks from intrusion using data and access controls. Examples include Data Loss Prevention (DLP), IAM (Identity Access Management), NAC (Network Access Control), and NGFW (Next-Generation Firewall) application controls to enforce safe web use policies.
- Application Security: Application security offers protection for web applications to prevent data or code from being stolen or manipulated. These safeguards are implemented during the software development process but involve patches, upgrades, and other approaches to protect apps after deployment.
- Cloud Security: Cloud security is the process of protecting data stored in the cloud from unauthorized access. While cloud computing providers manage the infrastructure, organizations that use their services must take extra precautions to secure their data.
- Infrastructure Security: Infrastructure security is the process of safeguarding critical systems and assets from cyber threats. This typically includes hardware and software assets such as end-user devices, data center resources, networking systems, and cloud services. Organizations must also protect their assets from physical threats such as natural disasters, utility outages, theft, or vandalism.
- Mobile Security: This is the process of employing user authentication and authorization across mobile devices, which is especially important as companies increasingly allow remote workers to use home Wifi networks.
- Internet of Things (IoT) Security: IoT-enabled devices, such as smart speakers, can be hacked and used to spy on people, as allowing devices to connect to the internet creates an additional attack surface for cybercriminals to exploit. IoT security seeks to end this.
Main Cyber Threats
Cybercriminals are continuously changing their strategies and uncovering new attack vectors. Here are some of the most common cyber threats you’ll see.
- Malware: Malware is any malicious software designed to infiltrate computer networks to steal data or cause damage. Some examples include viruses, worms, spyware, adware, and ransomware.
- Phishing: Phishing is the process of sending fraudulent communications, purported to come from a trusted source, but is in fact embedded with malware. Phishing emails typically contain links to a spoofed website (a fake website made to look like the original) or a malicious attachment to persuade the victim to divulge their personal information.
- Distributed Denial-of-Service (DDoS) Attack: A DoS attack occurs when hackers flood a server with internet traffic to prevent legitimate users from accessing a website or application. DDoS uses a network of “zombie” computers coordinated by multiple botnet machines that instruct infected competitors to flood a website with fake requests.
- Data Breaches: Hackers often attempt to gain access to a company’s servers or cloud storage to steal sensitive or confidential information. This is called a data breach.
- SQL Injection: A code injection technique that can destroy a database. It allows an attacker to interfere with the queries an application makes to its database by inserting malicious SQL statements into an entry field for execution (i.e. instructing the database to dump the database contents to the attacker).
- Ransomware: Ransomware is any type of malware that restricts access to a computer system, locks authorized users out of the system, or severely hampers system performance. Attackers will demand a ransom in exchange for the restoration of access.
Understanding the Cybersecurity Specialist
Cybersecurity specialists perform a range of tasks, from risk assessments to incident response. Security professionals may have expertise in a particular vendor’s product or experience in specific domains such as mobile applications. Let’s break down what that looks like.
What Does a Cybersecurity Specialist Do?
Cybersecurity specialists secure information systems by monitoring, detecting, investigating, and responding to security events. Here’s how they do that:
- Identify and Assess Cybersecurity Risks
- Develop and Implement Security Policies and Measures To Mitigate Risks
- Conduct Cybersecurity Audits
- Respond to Cybersecurity Incidents
- Maintain Up-to-Date Knowledge of Cybersecurity Threats and Trends
- Monitor Potential Data Breaches and Investigate if Needed
Cybersecurity Tools

Source: Javatpoint
Now that we know what a cybersecurity professional does, let’s take a look at the tools they use to make that happen:
- Intrusion Detection and Prevention
- Packet Sniffers
- Firewall
- Penetration Testing
- Cryptography
- Virus and Malware Protection
- Access Control
- Endpoint Security
Cybersecurity Career Opportunities
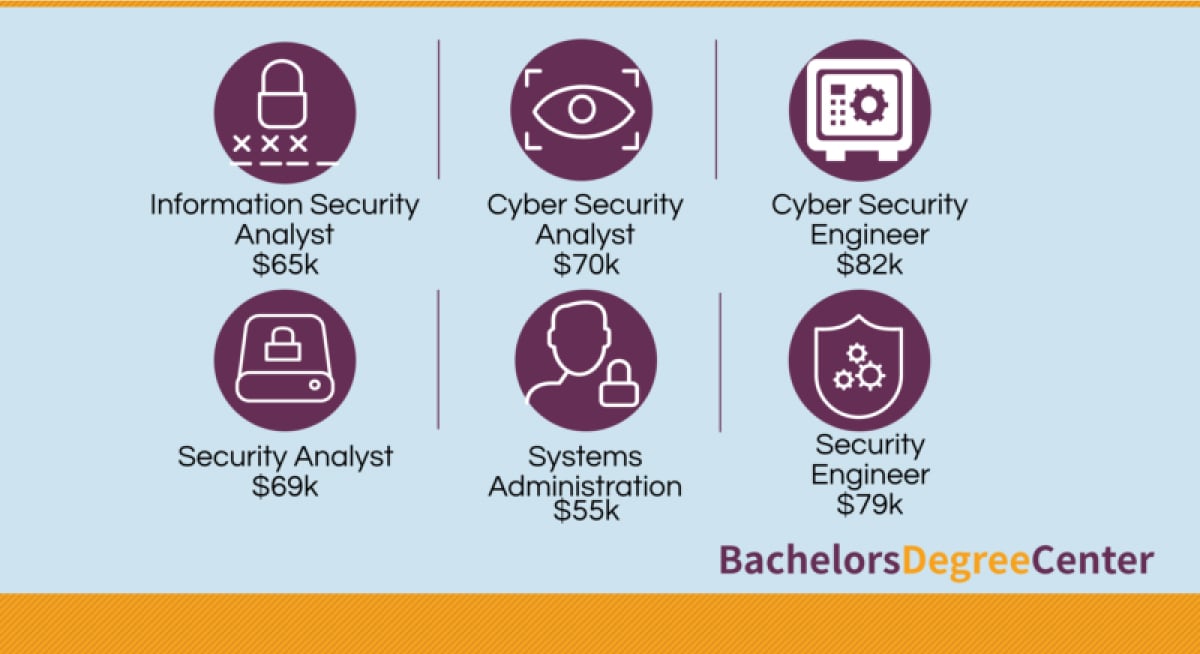
Source: BDC
A study by Burning Glass showed that cybersecurity job postings grew by 94% between 2013-2019, and now account for 13% of all IT jobs. With cybercrime growing increasingly prevalent, organizations are investing heavily in cybersecurity controls. Here are some of the most common cybersecurity career opportunities:
- Information Security Analyst
- Incident Response Analyst
- Risk Analyst
- Penetration Tester/Ethical Hacker
- Security Engineer
What Skills Do You Need in Cybersecurity?
Cybersecurity is a challenging and dynamic field that demands a diverse set of skills. These skills can be broadly categorized into technical and soft skills.
Technical skills are foundational. Knowledge of programming languages like Python, C/C++, JavaScript, SQL, and PowerShell/Bash is crucial for automation, scripting, and securing applications. Understanding TCP/IP, network protocols, firewalls, VPNs, and intrusion detection systems is essential for protecting network data. Proficiency in Windows, Linux/Unix, and MacOS security features is necessary for managing and securing various operating systems.
Soft skills are equally important. Problem-solving abilities, including analytical thinking, creativity, and attention to detail, are key for addressing complex security issues. Critical thinking skills, such as decision making, risk assessment, and continuous learning, are crucial for staying ahead of threats. Effective communication, collaboration, and leadership are important for teamwork. Flexibility, including adaptability, resilience, and time management, helps navigate the ever-evolving security landscape.
Success in cybersecurity requires a blend of these technical and soft skills. Continuous learning and adaptability are essential as the cybersecurity landscape is ever-changing.
FAQs About Cybersecurity
Cybersecurity is a good career choice for professionals who want a high starting salary and opportunities for advancement. The US Bureau of Labor Statistics predicts that employment for information security analysts will grow 33% from 2020-2030, much faster than the average growth rate for all occupations.
The shortage of cybersecurity professionals gives job seekers more bargaining power. According to Cybersecurity Ventures, the number of unfilled cybersecurity jobs worldwide grew by 350% from 2013 to 2021. The study predicts that the same number of jobs will remain unfilled by 2025.



On your place I would address for the help in search engines.
https://www.prolink-directory.com/Podgorica-Airport-Car-Hire_328232.html